Cyber attackers are now faster, smarter and more organised than ever before in the unstable world of cybercrime. They are always changing their tactics and they do it faster than the regular defence strategies can keep up.
This means one thing for business leaders: having cybersecurity controls in place is no longer enough. You must test your defences in real-life attack situations.
This is where a red teaming service comes in handy. Red Teaming is different from regular vulnerability assessments or audits that are done for compliance. Instead, it focusses on replicating real, multi-vector attacks to see how well your organisation can detects and deal with real threats.
In this article, we’ll talk about why red team exercises are now very important for making executive decisions. What kinds of threats they find, and how they help companies go from being reactive to being truly cyber-ready.
What is a Red Teaming Service?
A red teaming service is a high-level cybersecurity test that uses the same tactics, techniques and procedures (TTPs) that real attackers use. The Red Team, a group of ethical hackers, runs these tests to see how well your organisation’s technology, people, systems and response capabilities work together.
Standard penetration tests look for weaknesses in systems or applications, but red team exercises look at the whole security ecosystem of your organisation. From network infrastructure and applications to how people behave and how incidents are handled.
Basically, a red teaming service is basically the best way to test how strong your cybersecurity is.
What Specific Threats, Vulnerabilities or Attack Scenarios are Measured in a Red Team Engagement
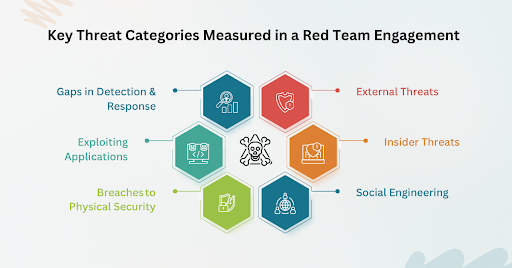
In a Red Team Engagement, the main areas and types of threats that are measured are:
1. External Threats
The red team pretends to be attackers from outside the company, using things like internet-facing systems, cloud vulnerabilities or misconfigured web apps.
2. Insider Threats
Red teamers might pretend to be an internal employee or a compromised user account to test your organisation’s ability to gain more access and steal data.
3. Social Engineering
The team tests how aware and responsive employees are to real-world deception tactics. They use phishing campaigns, impersonation or even phone-based manipulation.
4. Breaches to Physical Security
Advanced red team operations may include trying to get around physical security by tailgating or putting rogue devices inside buildings.
5. Exploiting Applications
Red teams use well-known tools like Cobalt Strike, Metasploit, Burp Suite to take advantage of flaws in applications, APIs and settings.
6. Gaps in Detection & Response
The most important aspect is to test the Security Operations Center (SOC) or blue team’s ability to find and deal with active threats.
These simulations show not only where weaknesses are, but also how quickly they can be used against you. This gives you a very clear picture of your organisation’s readiness.
What are the Key Benefits of Red Teaming for Organizations?
Before talking about the benefits, note that Red Teaming isn’t just about finding weaknesses; it’s also about making the whole organisation more coordinated, aware and resilient.
1. Realistic Attack Simulation
Red team exercises are different from regular tests because they replicate complex, multi-phase attacks that use the same strategies as real enemies. This gives you a real-life test of how well your defences hold up under pressure.
2. Better Detection & Response
A red teaming service shows how quickly and effectively your security team can find, contain and reduce active threats by putting them to the test. It also shows where monitoring and alerting are lacking or insufficient.
3. Stronger Incident Response Processes
Red Team engagements help improve incident response plans by making sure that when real incidents happen, they are handled faster, with better communication, and with coordinated efforts.
4. Improved Employee Awareness
Social engineering scenarios show how workers react to deception. It helps to build a culture of cyber vigilance across the whole organisation.
5. Informed Security Investment Decisions
Red team reports help business leaders to allocate better budgets by identifying which weaknesses are the most dangerous to the business.
6. Regulatory and Executive Confidence
Red teaming shows auditors, clients and boards that you are serious about keeping your cybersecurity strong by using proactive defence strategies.
Ultimately, the best benefit is that it translates technical data into strategic resilience and aligns cybersecurity with business goals.
What Makes Red Teaming Different From Regular Security Testing
Let’s look at how red teaming is different from other types of testing:
| Aspect | Vulnerability Assessment | Penetration Testing | Red Teaming Service |
| Purpose | Identify known vulnerabilities | Exploit specific weaknesses | Simulate real-world attacks |
| Scope | Limited to systems or apps | Focused technical scope | Organization-wide testing |
| Approach | Automated scanning | Manual exploitation | Strategic, stealth-based simulation |
| Outcome | Vulnerability list | Technical risk report | End-to-end readiness assessment |
Next Steps
If you are looking for stronger overall security for your organisation you should definitely consider red teaming service as a next step:
Here’s how to begin:
- Set clear goals. These goals can be testing your SOC, checking how ready you are for phishing, or making sure your cloud security is good.
- Make sure your provider uses advanced red team exercises that mimics how modern enemies act.
- Make sure to have debriefs after engagements so that you can turn those lessons into long-term defence plans.
If you’re looking for professional red teaming, you should think of working with well-known cybersecurity companies like CyberNX. Their full red teaming services use trusted frameworks and tools to imitate advanced, multi-stage cyberattacks. This helps organisations find their weak spots and make their people, processes and technology stronger.
Conclusion
Cybersecurity doesn’t just involve getting rid of all risks. It’s also about knowing how to deal with them when they happen. A red teaming service gives business leaders that information, turning uncertainty into useful information.
Realistic red team exercises can help organisations find weaknesses, improve the way they detect threats, and feel more confident in their cybersecurity.
In a world where attackers are brutal, the best way to stay afloat is proactive testing.

